Five Strategies to Optimize Cloud Security
How to Select the Right Zero Trust Network Access Vendor
In 2021, ZTNA inquiries from our end-user clients increased more than 50% year over year
Learn about the roadblocks that other organizations have encountered and strategies that are helping them move forward.
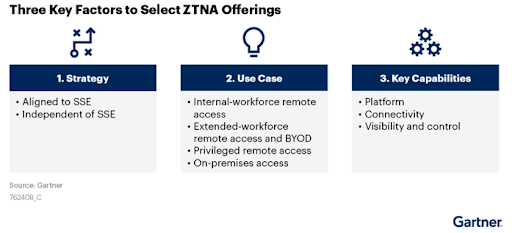
Learn to map your security needs to the four main use cases of ZTNA:
- Internal-workforce remote access
- Extended-workforce remote access and BYOD
- Privileged remote access
- On-premises access
Shortlist ZTNA vendors by focusing evaluations on three key offering capabilities including platform, connectivity and control.
See how future Security Service Edge strategy can influence your ZTNA decisions regarding Agent-Based vs. Agentless ZTNA and the following…
- Remote Browser Isolation (RBI)
- Data Loss Prevention (DLP)
- Web Application and API Protection (WAAP)

3 Comments
Jonson Lara
Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat possimus omnis voluptas assumenda est, omnis dolor repellendus.
Rosailina William
Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat possimus omnis voluptas assumenda est omnis dolor repellendus est eligendi optio.
admin
Cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat possimus omnis voluptas est omnis dolor repellendus temporibus autem quibusdam.